A little while ago, NSS Labs released a report on how the different browsers (IE, Firefox, Chrome etc.) handled malware. And, it appears for the type of malware tested, Microsoft browsers (IE8 good, and IE9 best) kick some malware butt.
NSS Labs report found that IE (8/9) identified and caught over 90% of the malware threats while the other competing browsers Safari, Chrome and Firefox caught roughly 13% of the threats. The fact that these three browsers had similar results is not surprising as they all use the same filtering technology.
Microsoft's IE8 and IE9 use a Smart Filtering technology that scans each URL and executable (EXE) to see if has a digital signature and whether it has been downloaded by other people previously. Though there is a potential for false positives, this system appears to be able to "react" quickly to new threats and block a significant profile of malware threats.
You can read more about the Microsoft Browser Smart filtering technology here: http://blogs.msdn.com/b/ie/archive/2011/05/17/smartscreen-174-application-reputation-in-ie9.aspx
You can read more about how an add-in for Visual Studio fell foul of the Smart Filter rules here: http://www.itwriting.com/blog/4533-this-is-why-people-ignore-security-warnings-ie9-blocks-official-microsoft-update.html
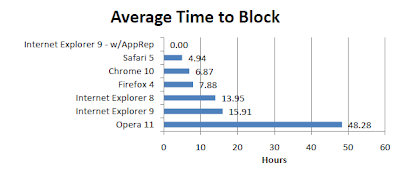
The report is well presented and very accessible and the results clearly demonstrate one thing: the approach Microsoft has taken with IE and IE9 when dealing with malware clearly works as you can see by the following diagram on the response time to block a potential malware executable.
Straight from the source, Microsoft heavily promotes the security features for IE9 with the following key features;
- IE8 is the only browser to block XSS attacks “out-of-the-box.”
- IE8 introduced the first “out-of-the-box” mechanism to allow sites to prevent ClickJacking attacks.
- IE8 introduces new functions which allow sites to build more-secure mashups (toStaticHTML(), XDomainRequest) and supports new standards-based mechanisms (Native JSON support, postMessage()).
- Safer default settings (DEP/NX, per-site AX) mean that users are better-protected than ever before. Group Policy controls (for ActiveX management, enforced SmartScreen blocking, etc) allow IT administrators to reduce the number of trust decisions users face when using IE8.
I am looking forward to the industry response to this report. Will we see Google say that NSS Labs is in the pocket of MS? Will they dispute the source URL's or EXE's? Or, will they get their act together and implement a proper protection system - cloud based, collaborative, crowd-sourced or whatever... Something.
You can find the NSS Labs report in its entirety here:
http://www.nsslabs.com/assets/noreg-reports/2011/nss%20labs_q2_2011_browsersem_FINAL.pdf